BND threatens to sue wikileaks
20 Dec 2008BND threatens to sue wikileaks:
http://wikileaks.org/wiki/German_spy_chief_threatens_Wikileaks
BND threatens to sue wikileaks:
http://wikileaks.org/wiki/German_spy_chief_threatens_Wikileaks
IP address ranges have been leaked to wikileaks. I wrote a quick ‘n dirty shell script to parse my webserver access log files for these IP ranges.
#!/bin/bash
CountIpRanges ()
{
(cat <<EOF
193.159.228.32 - 193.159.228.39
193.159.238.168 - 193.159.238.175
194.25.184.16 - 194.25.184.23
194.25.42.232 - 194.25.42.239
195.145.128.56 - 195.145.128.63
195.145.163.64 - 195.145.163.127
195.145.182.96 - 195.145.182.111
195.145.31.252 - 195.145.31.255
195.145.57.176 - 195.145.57.191
195.243.157.184 - 195.243.157.191
195.243.248.224 - 195.243.248.231
212.185.184.224 - 212.185.184.231
212.185.191.128 - 212.185.191.135
217.7.155.168 - 217.7.155.175
217.89.74.208 - 217.89.74.223
62.153.59.192 - 62.153.59.223
62.153.65.32 - 62.153.65.39
62.153.80.208 - 62.153.80.215
62.153.87.0 - 62.153.87.15
62.154.211.152 - 62.154.211.159
62.154.226.64 - 62.154.226.127
62.156.187.232 - 62.156.187.239
62.157.136.64 - 62.157.136.95
62.157.144.0 - 62.157.144.63
62.157.193.128 - 62.157.193.223
62.157.194.32 - 62.157.194.39
62.159.19.208 - 62.159.19.215
62.159.104.160 - 62.159.104.175
62.159.209.144 - 62.159.209.151
62.159.209.152 - 62.159.209.159
62.159.21.152 - 62.159.21.159
62.159.60.144 - 62.159.60.151
62.159.63.72 - 62.159.63.79
62.225.139.248 - 62.225.139.255
62.225.74.128 - 62.225.74.135
80.146.198.88 - 80.146.198.95
62.159.104.160 - 62.159.104.175
EOF
) | sed 's/ //g' | awk -F- '{ split($1,IPS,".") ; split($2,IPE,".") ; \
for (I=IPS[4];I<IPE[4];I++) { print IPS[1]"."IPS[2]"."IPS[3]"."I } }'
}
CountIpRanges | grep -H -f - $1
I posted some of my “featured” photographies on my new deviant art profile, enjoy ![]()
Today I was playing around with my new Canon 450D DSLR and did a “HDR” experiment.
The original picture, a view into my garden photographed out of my window. As you can see, its a bit overexposed:

And a processed HDR made out of three pictures done in bracketing mode:

Compare the two images with a mouseover effect (needs javascript).
My idea was to build/simulate a typical firewall setup with a redundant firewall, where the secondary box takes over if the primary fails. After considering a Linux based solution, I decided to try a BSD based approach, since this OS family seemed very suitable for this kind of setup.
After playing around a bit with some open source based firewall appliances like m0n0wall and pfsense, I did what real men do - and settled for OpenBSD ![]() The following draft shows the setup I am planning to implement:
The following draft shows the setup I am planning to implement:
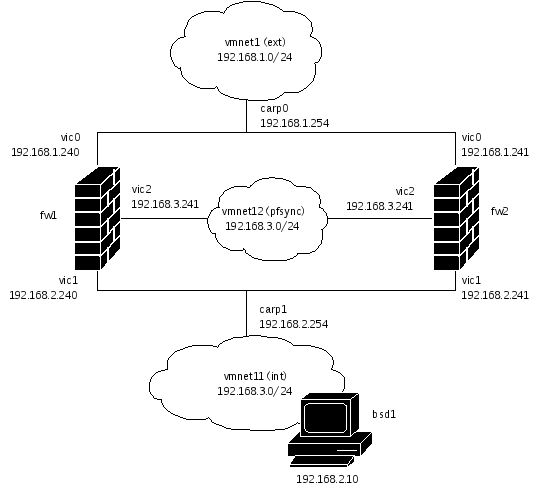
So basically we have the following components:
The external network: ext, 192.168.1.0/24
The internal network: int, 192.168.2.0/24
A special network between the firewalls: pfsync, 192.168.3.0/24
The firewalls have their “own” IP addresses: fw1, x.y.z.240 and fw2, x.y.z.241, where x.y.z are the networks int,ext and pfsync
Both firewalls share “virtual” IP addresses: 192.168.1.254 on ext and 192.168.2.254 on int
In the int network, we have a workstation bsd1 with the IP 192.168.2.10
Normally fw1 operates as primary firewall and filters/forwards packets between ext and int. If a failure occurs, fw2 takes over the virtual IP addresses and operates as firewall/gateway. The pfsync network is a special network between the firewall, reserved for special firewall communication like state syncing.
And since we haven’t got that much spare hardware lying around, we will simulate this scenario with virtual machines based on a VMware server setup.
Since VMware server really has its quirks in this kind of setup, stay tuned for part II: VMware server setup